Photographs: Kacper Pempel/Reuters Ashish Sharma In New Delhi
It is Saturday night and Suzanne (name changed) is in her Miami home, hunched over her laptop. The house is quiet, save for the keyboard tapping, when a message from nowhere pops on her screen: "Hi Suzy."
The 19-year-old feels a chill. She is visible from afar on a hacker's computer. He has taken control of her machine with a remote administration tool, rat in short, and is now able to see her through the webcam, rummage her files and listen in through her microphone.
…
Behind the scenes: How hackers take control of your life
Image: A girl surfs the net.Photographs: Reuters
Next, her mouse and keyboard freeze and a Notepad file starts typing - by itself. She looks up: the tiny light beside her webcam glows.
She gazes fearfully into the lens, wondering if someone's watching, when a message pops again, saying the hacker knows all about her.
To prove it, he starts talking about her room, the colour of her walls, the pattern on her sheets, and her Facebook messages. Scared out of her wits, she reaches for the power switch and flicks it off.
Image for representation purpose only.
…
Behind the scenes: How hackers take control of your life
Image: A man wearing a Guy Fawkes mask surfs the web.Photographs: Nacho Doce/Reuters
Far away, the hacker, Sachin, opens his control panel, on which he can see all his victims, or 'slaves', through their webcams. Besides providing a host of fun tools for messing with his slaves, the panel shows their locations and the status of their machines.
"I can hide their Windows Start button or the taskbar or the clock or the desktop or record their keystrokes and, thereby, their passwords," he says in an email interview.
"Ratting is easy," says Sachin. "It is the setting up of the software which is difficult."
Image for representation purpose only.
…
Behind the scenes: How hackers take control of your life
Image: Spreading Guide v7.0.Photographs: Courtesy, hackforums.net
For those who can't manage on their own, best-seller author Sachin hawks his expertise on hackforums.net in the latest edition of his e-book, Spreading Guide v7.0, which costs £15 (around Rs 1,500).
Readers are told they can pick up to 3,000 slaves a day. And if this handholding isn't enough, one can simply buy slaves from more successful ratters for up to $50 a piece.
"The auction market for slaves has been good and consistent. The US slaves come cheap as there are too many of them. Everyone's got the US covered," says Sachin, who narrated the Suzanne story.
…
Behind the scenes: How hackers take control of your life
Image: Remote administration tool BlackShades.Photographs: Courtesy, BlackShades
Also, Sachin chillingly discloses, "people offer free coaching for beginners on Skype". A 15-year-old from Amsterdam who goes by the name of Blue Sky on hackforums.net says he is a mentor to many.
"The basics of cyber-peeping haven't changed much: just get your target to download an e-mail attachment or …
Behind the scenes: How hackers take control of your life
Image: Participant hold their laptops in front of an illuminated wall.Photographs: Patrick Lux/Getty Images
To fish for slaves, many employ social engineering tricks. Lonely Fox messages random people on Facebook and infects them. "With the right words, anything is possible."
There are others who make drive-by sites that look like a picture from Facebook and say something like "this is an ugly picture of you" or "is this you in the picture?" This tempts some to …
Behind the scenes: How hackers take control of your life
Image: An employee works near screens in the virus lab at the headquarters of Russian cyber security company Kaspersky Labs.Photographs: Sergei Karpukhin/Reuters
Some create a fake Facebook account, and 'like' a few Justin Bieber pages and start commenting on them: "Check out my new Bieber screensaver, it's so hot."
A link is given. "Think of the thousands of people going on those pages by the minute, you will definitely get some gullible bots," says Fox.
"Poor people," says Sachin, "They think they are alone in their homes, but have no idea they are the laughing stock of the underground people."
…
Behind the scenes: How hackers take control of your life
Image: A man types on a computer keyboard in Warsaw.Photographs: Kacper Pempel/Reuters
Ratters have complete control over the computers they infect. And these attacks are very silent.
DarkComet even has a Fun Manager that can perform all sorts of tricks on the target.
"To startle, I can open a chat window or the CD tray," Fox says. The purpose is to annoy people.
Spaceboy admits: "We are all going to hell for this."
Most other ratters tend to accept ratting as harmless fun. But morals generally take the back seat to mockery.
…
Behind the scenes: How hackers take control of your life
Image: A Chinese Worker Installs A Webcam.Photographs: Reuters
Fox says he posts pictures of his 'ugly slaves', some caught picking their noses. The hurdle is the webcam: its light glows every time the camera is in use, which can alert the victim.
"The first time I use a slave's cam, I send a fake Windows-like message saying the cam's software is updating and the light may go on and off," says Spaceboy. That puts off suspicion.
Pankaj Jain, director, ESET India, another maker of anti-virus software, says the light is tied to the camera physically, so it turns on when in use. "If a hacker can remove that bit of the software code which controls the light, he can disable it."
…
Behind the scenes: How hackers take control of your life
Image: A girl crying.Photographs: Reuters
Such footage could be used for blackmail. Or can cause trauma. Take 'Suzy', who shook uncontrollably, unable to collect herself.
After the incident, probably she couldn't concentrate on her studies. Probably she had holed up alone, away from family and friends.
Probably she felt 'terrorised' because someone had secretly burrowed his way into her hard drive, and then into her life, following her every move.
Image for representation purpose only.
…
Behind the scenes: How hackers take control of your life
Image: Marta Cruz, 17, from Helen Bernstein High School tries a prom gown.Photographs: Kevork Djansezian/Reuters
Ratters insist it is harmless fun. "Most stuff you would capture on a camera," says Spaceboy, "they've already posted on Facebook." So, a video of someone isn't going to yield much cash.
That brings us to the basic question: what drives the ratter? "Every young person I spy on," Fox says, "seems to be living the life I have been denied. These people are having fun: making plans for prom and going to parties. I have never had that. I am lonely all the time. So I rat them, thinking, oh, you do all these wonderful things, now why don't you have a bad day just like me?"
…
Behind the scenes: How hackers take control of your life
Image: A man handcuffed by police.Photographs: Gleb Garanich/Reuters
But do not try this at home. Cyber law expert Pavan Duggal says: "Hackers using rats to invade computers and spy on a victim through webcams and microphones is a breach of privacy. Such activities constitute the offence of hacking and computer-related offences under the Information Technology Act, 2000."
Prashant Mali, also a cyber-law expert, says the offence is punishable with three years' imprisonment or a fine of Rs 500,000 or both. "It is cognizable: the police can arrest without warrant."
Online forums that post and host information pertaining to ratting often cross the line into illegality. However, the Act is silent on rat software.
…
Behind the scenes: How hackers take control of your life
Image: Department of Homeland Security (DHS) researchers use advanced modeling and simulation equipment.Photographs: Ho New/Reuters
"But," Duggal says, "if a piece of software contains banned parameters, it would be illegal."
Funnily, rats were originally intended for industrial purposes such as controlling a system or monitoring a place through a webcam from afar.
"A number of times, software is made keeping in mind legitimate purposes. However, it is the illegal usage the law seeks to penalise," says Duggal.
…
Behind the scenes: How hackers take control of your life
Image: Norton AntiVirus 2010 Main Interface.Photographs: Tyw7 /Wikimedia Commons
How does one protect against becoming a slave to ratters? Chopra of Norton by Symantec says, "Keep antivirus definitions, operating systems, and software up-to-date."
Avoid opening emails from unknown senders and …
Behind the scenes: How hackers take control of your life
Image: Screenshot of opentopia website.Open, By Accident
It's eight in the morning and a woman sits at a hotel reception in Belgorod, Russia. A child is running around the place and the woman smiles at him.
Then a middle-aged man walks in with his luggage. Both trade hellos and the woman gets back to the child and makes friends with him.
The feed should be private, meant to be seen only by the manager. Somebody forgot to …
Behind the scenes: How hackers take control of your life
Image: Security cameras.Photographs: Charles Platiau/Reuters
France-based Flemming Funch, co-owner of the website with Patrick Cornwell, says: "I made an automated programme that found open webcams on Google, and went regularly to take a snapshot of each, to then present that in a gallery. It was a bit of a surprise how popular it became."
Indeed, the discussion forum for the hotel webcam seems to be active. A viewer says, "Wow, these girls at the reception just get to sit and drink. What kind of management do they have?" Another says, "I just looked it up on Google. The hotel has got four out of a five-star rating."
Many know their camera is accessible and enjoy the attention. Others pay the price for their forgetfulness.
"Some webcam owners might simply have left their camera open by accident. So, it appeals to the voyeur in many of us," says Funch.
…
Behind the scenes: How hackers take control of your life
Image: Paul Mathis, a.k.a., Restil.Photographs: Courtesy, drivemeinsane
Perils Of A Smart Home
Paul Mathis, 40, is working in his home in Texas, when, all of a sudden, a row of lamps goes off, and then comes on.
The ceiling fan starts whirring on its own and a four-wheeled robot activates its electric eyes and starts work.
All this may suggest the presence of a resident evil. But Mathis knows an Internet user, and not a ghost, is adding flicker to the lights.
Mathis, net name Restil, the creator of drivemeinsane.com, has brought his home automation project onto the Internet.
By going to the site, you can control his appliances such as lamps, disco ball, fan, icicle lights and the robot.
…
Behind the scenes: How hackers take control of your life
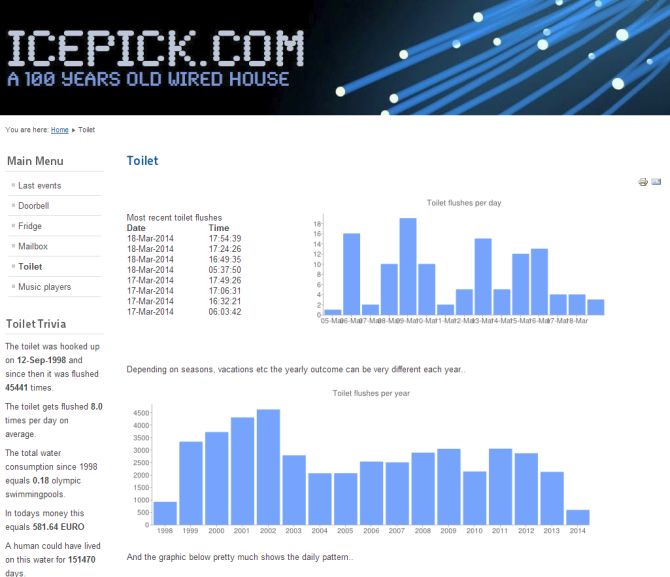
Image: Screenshot of Icepick website.An automated home consists of Internet-connected appliances that can be remotely controlled. The devices can talk to each other and even act on the owner's behalf.
Mathis is not alone in doing this. Icepick.com publishes data of an automated, or smart, home.
"The toilet of this house was hooked up on September 12, 1998. Since then, it has been flushed 45,338 times."
The site shares toilet trivia, too. "The total water consumption since 1998 equals 0.18 Olympic swimming pools. This equals 580 euros."
…
Behind the scenes: How hackers take control of your life
Image: Conservative protesters burn portraits of North Korea's Kim Jong-il (R) and his son Kim Jong-un during an anti-North Korea rally denouncing the North's cyber attacks.Photographs: Jo Yong Hak/Reuters
As everything, including homes and toilets, gets networked, there is an increasing likelihood of your personal data, such as flushes, getting into the clutches of a hacker.
One can simply type certain keywords on search engines and find the remote control panel.
This way, smart appliances can be used to launch attacks, physical and otherwise. Pankaj Jain, director, ESET India, says, "If someone doesn't set a username and password, anyone can have control."
…
Behind the scenes: How hackers take control of your life
Image: A man surfs the web.Photographs: Nacho Doce/Reuters
Also, finding the address of a hacked house should not be a problem, adds Jain. "If the systems show up in search results and if the login is not required, one can turn these homes into haunted houses, energy-consumption nightmares, or even robbery targets. Opening a garage door could make a house ripe for actual physical intrusion."
Opentopia.com has many webcam feeds from vacation houses. Jain suggests using firewalls, passwords and biometric verification systems for protection.



















article